Quantum Computing Supremacy has been reached! It can now outperform traditional computers.
What is quantum computing? Well, lets back up a bit.
Quantum computing is a emerging type of computing that is much different then the PC, Mac or mobile device. The traditional device in front of you right now creates your experience and processes your requests solely based on bits of binary code. Similar to a light switch, a CPU reads 0 for off and 1 for on. Amazingly, with enough of these 0s and 1s in a linear order, a traditional computer will create the experience of social media, a spreadsheet, solitaire “work” while on your lunch break, and ALL the other amazing things we use every day on a phone, tablet, or PC.
A quantum computer on the other hand, processes Qbits. Quantum Bits, Qbits, get it? A quantum computer also processes either on or off – or a combination of both at once (so a ‘1’ or a ‘0’ at the same time) – which the latter is where it gets confusing for most people as we start saying words like “phenomena” or “entanglement” to which I will spare you in this post. All you have to know is having Qbits allows the computer to process much larger math problems at far greater speeds.
Quantum Computers ARE in use… NOW!
OK, back to the nerdy talk. Despite what some online articles and some experts may say, in reality, quantum computers are already being used by nation-states for intelligence purposes. Here are a few articles that address the cryptographers challenges trying to meet this new threat:
Science Magazine – Cryptographers Scramble to Protect Internet Hackers from Quantum Computers
Medium.com – How Quantum Computers Will Break Your Phone’s Encryption
Wall Street Journal – The Race to Save Encryption
If you need more, connect with me on LinkedIn and we’ll get more in-depth together.
Encryption is Math. Math is not technology.
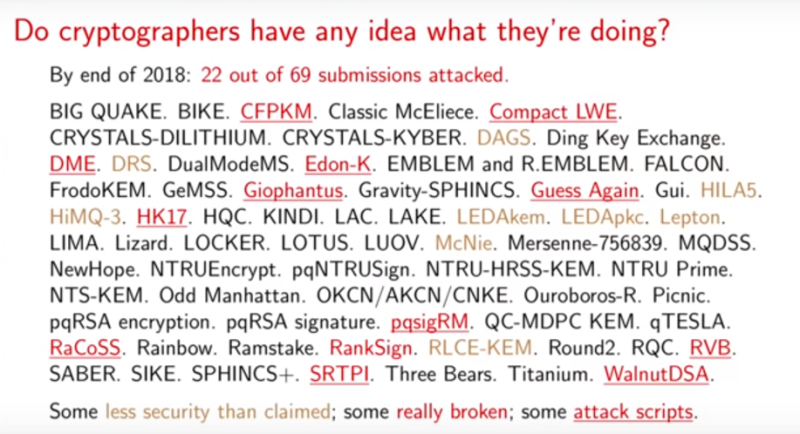
To add more weight to my previous posts about the death of encryption, it is not surprising that 69 quantum computing encryption algorithms have been submitted to NIST. 22 of them have already been hacked and based on those hacks the remaining ‘math based’ solutions are also vulnerable to the same attacks. When can we finally admit so long as we use math-based systems hacks will continue? (see DES, TripleDES, AES128, AES256, Blowfish, Lattice Encryption for details) What we need is a better approach and Secured2 is that approach. True data randomization. physical separation, data conversion and effort based user verification are the keys to a secure future.
Quantum computing supremacy is astounding news, as that’s the point where quantum computers can outperform the computational output of the most powerful traditional computers. We at Secured2 have to personally congratulate the team at Google for this incredible achievement!
However, with quantum computing getting into its next phase of growth, it also brings problems. Thankfully, Secured2 is proven to solve many of those problems either through our products directly or a customized data security solution to your needs using our SHRINK > SHRED > SECURE > RESTORE patented data security process.
Written by:
Daren Klum
CEO
SECURED2 Corporation